Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
Physical Address
304 North Cardinal St.
Dorchester Center, MA 02124
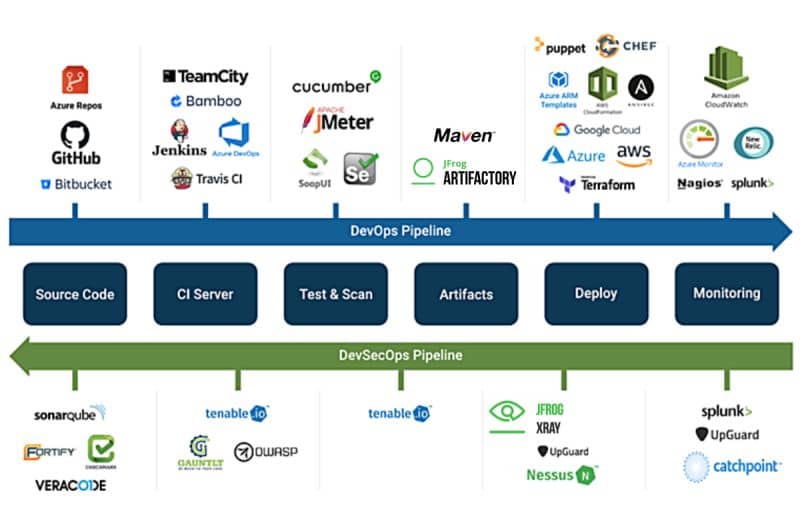
In today’s world, security is an essential aspect of software development. DevOps, with its focus on continuous integration and continuous delivery, has become a popular software development approach. However, security in the DevOps pipeline is often overlooked, leaving applications vulnerable to attacks. Therefore, it is necessary to integrate security tools into the DevOps pipeline to ensure secure software development. In this blog, we will discuss some security tools that can be used in the DevOps pipeline, along with examples of those tools.
Static Application Security Testing (SAST) is a security tool that examines source code for security vulnerabilities. SAST tools analyze the code before it is compiled or executed and detect potential security risks such as SQL injections, cross-site scripting (XSS), buffer overflows, and other code vulnerabilities. Examples of SAST tools include:
Dynamic Application Security Testing (DAST) is a security tool that analyzes running applications to detect vulnerabilities. DAST tools simulate real-world attacks by sending malicious inputs to the application to identify vulnerabilities such as SQL injections, cross-site scripting (XSS), and other vulnerabilities. Examples of DAST tools include:
Interactive Application Security Testing (IAST) is a security tool that combines the benefits of SAST and DAST tools. IAST tools analyze the code while it is running to detect security vulnerabilities. IAST tools can detect vulnerabilities such as SQL injections, cross-site scripting (XSS), and other vulnerabilities. Examples of IAST tools include:
Vulnerability scanning is a security tool that identifies vulnerabilities in the operating system, network, and applications. Vulnerability scanning tools can be used in the DevOps pipeline to identify potential security risks before they can be exploited. Vulnerability scanning tools can detect vulnerabilities such as unpatched software, open ports, weak passwords, and other vulnerabilities. Examples of vulnerability scanning tools include:
Container security is a security tool that focuses on the security of the containers used in the DevOps pipeline. Containers are lightweight virtualization technologies that can be used to package an application and its dependencies. Container security tools can detect vulnerabilities in the containers, such as unpatched software, weak passwords, and other vulnerabilities.
Identity and Access Management (IAM) is a security tool that ensures that only authorized users have access to the DevOps pipeline. IAM tools can provide authentication, authorization, and access control to ensure that only authorized users have access to the pipeline. IAM tools can be integrated into the DevOps pipeline to improve security.
In conclusion, security is an essential aspect of the DevOps pipeline, and there are several security tools available to improve the security of the pipeline. These tools can help to identify potential security risks, detect vulnerabilities, and ensure that only authorized users have access to the pipeline. By integrating these security tools into the DevOps pipeline, organizations can improve the security of their software development process and protect against potential security threats.